Have you ever wondered how many unauthorized login might be attempted on any service exposed to the internet? In this article I'm going to explain how I trace all the attempted logins on my SSH box to get an idea of how many badguys are there on the internet.
My setup:
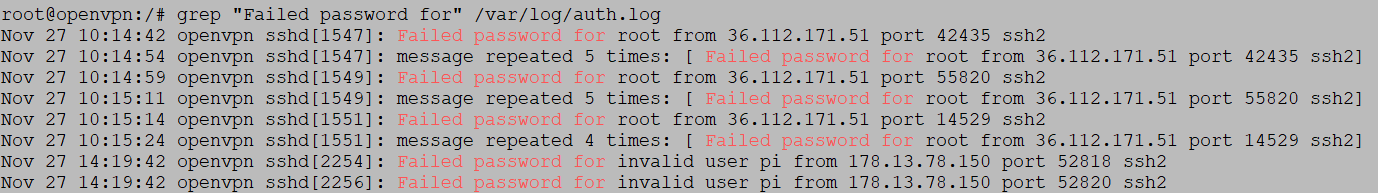
Failed login attempts can be feteched searching for "Failed password for" in /var/log/auth.log (log file might be different based on your distro):
grep "Failed password for" /var/log/auth.log
Sample output:

We might have 2 different kind of message depending on whether the user is “valid” (i.e. exists, like root) or not on the SSH box; so in order to extract sensible data I've built this one-liner:
grep "Failed password for" /var/log/auth.log | awk '{print
$(NF-3)}' | sort | uniq -c | sort -gr -k1
Explanation:grep "Failed password for" /var/log/auth.log
Extract the lines for each failed login attempt
awk '{print $(NF-3)}'
for each line, extract the last-fourth column only which contains the
source IP address
sort
Result are sorted (for the sake of the next command)
uniq -c
Extract only unique occurrences of every source IP
sort -gr -k1
Results are sorted again to create a top-n list
In the end, take a look here where you can find all the logs I'm collecting every once in a while: https://www.readonlymaio.org/sw/index.php?b=badguys
Using the same approach above, we can extract the list of the (distinct) usernames used and build your own users dictionary:
grep "Failed password for" /var/log/auth.log | awk '{print
$(NF-5)}' | sort | uniq
Here you can find the list of all the usernames used by the badguys: https://www.readonlymaio.org/sw/badguys/badguys_usernames.txt